Many security and IT teams suddenly have to support and protect employees who must work remotely due to the COVID-19 crisis. Make sure you cover these areas.
By Susan Bradley, Contributing Writer, CSO
Your boss just called and all your employees are mandated to work from home for the next two to three weeks due to the potential COVID-19 pandemic. What could go wrong? What risks are you now bringing to the firm? These are the actions should you take immediately to ensure you can allow your workforce to work remotely and securely.
1. Determine what endpoint protection you will require for home users

While you may have consoles and the ability to manage all the workstations at your physical office, you do not have the same level of control for home computers. Windows Defender included in Windows 10 is a more than acceptable antivirus tool for a remote machine.
Any remote worker that has a Macintosh should not be exempt from using endpoint protection software. One in ten Mac users have been attacked by the Shlayer Trojan.
Set a policy that all home employees must use an antivirus tool on the machines that access the firm’s resources. Consider if you need to deploy alternative cloud-based means to monitor workstations. Review what support console tools you use now and the necessary licenses you may need to access computers that are not part of your domain. You can quickly set up tools such as Splashtop SOS or LogmeinRescue to allow your IT support team to remotely access employees’ home machines to assist in setting up remote access.
2. Review what software remote employees need
For Office 365 subscribers, some of the licenses allow you to install the Office suite on up to five PCs or Macs, five tablets and five smartphones. Those with Volume licenses can allow Office for home use purchases for your employees. You may need to review your options and licensing alternatives based on what platform and version of Office you are currently licensed for.
You may want to add the ability to manage and monitor the remote systems of your users if they are not already under your control. Review what options you have with your current antivirus vendors to see if they have cloud consoles that can be easily used to manage these remote machines. Alternatively, if you have Office 365, you can use Intune with the proper licensing. Finally, reach out to consultants that you use; they may be able to provide temporary licenses with screen connection software that they already use to remotely manage your network.
Microsoft is also offering six months of Teams for free to allow users to better work remotely. In addition, Windows Virtual Desktop on Azure can be combined with Office 365 Pro Plus to provide additional resources to your users.
The use of Teams by those not used to working remotely may mean that you’ll need to review privacy policies and secure information handling with employees. Users may inadvertently expose information during video calls, for example. Review proper handling of documents and sensitive communication with personnel. Consider providing overall guidance on how to handle remote working that includes communication, well-being checks, and reviewing what equipment will be needed for the process.
3. Ensure remote access does not introduce more risk

You may have to suddenly set up and license remote access servers, Windows 10 virtual desktops or other remote technologies. Don’t introduce more risk in terms of licensing and security risks based on the decisions you make. For remote access that includes remote access services, remember that ransomware attackers look and scan for open RDP servers, targeting anything responding on port 3389. Don’t move RDP to another port as TSgrinder scans for an RDP response on any port.
Do not blindly open remote access ports without thinking of the risks and consequences accordingly. If you must open remote access, ensure that the firewall is configured to only respond to certain static IP addresses from which your IT administrators will be remotely accessing.
4. Implement two-factor authentication (2FA)
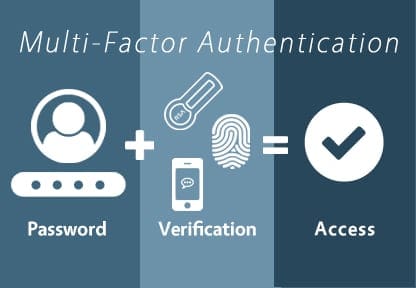
When adding more remote access solutions, consider adding 2FA to remote access solutions. You can easily add 2FA solutions such as DUO.com to existing on-premises remote access solutions. DUO.com can add 2FA to RDGateway and Remote Web Access solutions. While your firm may need to move quickly to allow your staff to work remotely, you can still ensure that only those admins and users are allowed in and not any attackers as well.
5. Use a virtual private network (VPN)
Recently there have been several high-profile vulnerabilities in VPN software. Often on client workstations that have not been updated in years, an older version of VPN software has been left behind. Ensure that your VPN solutions are up to date both on the server or firewall that is providing the VPN solutions, or on the desktops of the remote user.
6. Assess the impact to firewalls, conditional access policies and other logging
Your firm might have a security information and event management (SIEM) logging solution that looks at traffic coming from local desktops and laptops to server resources. If your entire workforce traffic suddenly comes in from various IP addresses, your logging platform data will no longer be “normal”.
Those who use geoblocking in the firewall to restrict access from different locations will need to review and revise those policies given that your firm’s employees will be coming in from various locations. You may also need to increase internet bandwidth for inbound traffic to your organization. For those who rely on cloud services, you may need to diagnose and determine if home users have appropriate bandwidth to support Office work and possibly video conferencing.
You also may find that the security settings of consumer firewalls and internet providers block some of your intended remote access. For example, Comcast’s advanced internet security blocks the use of RDgateway over port 443. You may need to review connection logs, get security logs from your remote users, and add more resources to your help desk to help users connect remotely.
7. Educate employees on COVID-19 scams

The National Cyber Awareness system warned of COVID-19 scams that are circulating. Urge your users to not click on unsolicited emails and to use only official websites. Ensure that the firm has a central online bulletin board that they go to for official communication and notification, especially if anyone in your organization becomes infected.
8. Update acceptable use policies for employees
Finally, ensure your acceptable computer use policies cover employees’ home computer assets. If this wording is not already there, you’ll need to quickly get up to speed in allowing employee’s personal assets be used for remote access. You’ll need to work with the firm’s attorneys and tax advisors to see if the use of personal computers and personal phones of the employees mandate a need for reimbursement for use.
Planning for the future

While this is a stressful time given the uncertainties, it’s also a great time for seeing how ready your organization is for emergencies and other remote worker needs. Even if you don’t tell everyone to work from home, take the time to think about if you could make everyone work from how and how well you could do it. Review the CIS Telework and Small Office Network Security Guide to see if there are any other security issues you should be monitoring.
Read the full article here
Contact O2 to see how we can help your organization at GetResults@O2ConsultingGroup.com







